- GRC Engineer - Engineering the Future of GRC
- Posts
- ⚙️ The GRC Engineering Implementation Framework That Works for Enterprises (no more DIY failures)
⚙️ The GRC Engineering Implementation Framework That Works for Enterprises (no more DIY failures)
A 5-step methodology that addresses coordination challenges, leverages existing infrastructure, and delivers business value without creating the technical debt that kills most initiatives
IN PARTNERSHIP WITH

Auditors engineered for the public cloud.
Complex environments demand skilled assessors who understand modern tech stacks and know how to architect secure infrastructure. That’s why Google, Microsoft, and Grammarly trust Mastermind as their certification auditor for ISO standards—these audits are literally all we do.

What’s going on? 🔊
Chatting and collaborating with the one and only, Michael Rasmussen
If you don’t know Michael Rasmussen, you probably don’t know GRC! He literally was involved in coining the term GRC itself and has been the main industry analyst in this space for decades.
He’s a good friend of mine and we’ve chatted about GRC Engineering and the overall market pretty often. He’s probably the most knowledgeable and well connected GRC Industry Analyst out there.
I was on his podcast Risk is our Business where we chatted about GRC Engineering and the following topics in just 20min:
What GRC engineering is, what it does, the value it provides.
Moving GRC away from after-the-fact verification and closer to the design phase, where software engineering problem-solving can be applied to solve long-standing compliance and assurance challenges.
The core elements of GRC engineering
Where it should be applied, and ask whether its cyber-heavy focus today limits its potential, or whether it’s destined for broader adoption across enterprises.
If you prefer reading, he wrote a deep-dive on GRC Engineering based on our interview and really augmented my points with his rich experience and insights working with enterprises across the globe.
Planning on having him on the GRC Engineer podcast as well pretty soon 😃
Check it out ⬇️
Here’s to more collaboration and working together towards the GRC revolution!
An interesting LinkedIn post you should check out 📊
How can we create role clarity in GRC based on how the data teams evolved!
The data industry solved role clarity 15 years ago whilst the GRC industry is still debating what "technical" means. This LinkedIn analysis draws parallels between data team evolution and where GRC is heading.
The data evolution pattern:
2010: Everyone was a "data analyst" doing SQL and Excel
2015: Clear role differentiation emerged based on problem domains
2025: AI reshapes how each role works but doesn't blur role boundaries
The proposed GRC parallel:
GRC Analyst: Business intelligence, control testing, audit preparation
GRC Engineer: Infrastructure, automation, system integration
GRC SME/Principal: Strategy, programme architecture, risk-driven design
The key insight: just as data analysts use AI tools without becoming data scientists, GRC analysts can apply engineering thinking without writing Python. Role clarity drives industry maturity - when you know whether you need pipeline engineering or statistical modelling, you hire accordingly.
The challenge for our industry is moving beyond the current "everyone's a GRC professional" ambiguity towards the specialisation that enables scale. The data industry's transformation from "spreadsheet people" to strategic business function happened once roles and value became clear.
This analysis connects directly to the implementation framework above - understanding whether you need GRC Engineering (systems/process) or GRC Engineers (technical skills) becomes clearer when we have defined career paths and role boundaries.
I’m planning to think more about these topics
For this week

The 5-Step GRC Engineering Implementation Framework 🔍
Why successful automation requires systems thinking, stakeholder alignment, and boring solutions
We’ve chatted about DIY GRC Automation is breaking at Enterprise Scale and the reasons why it’s tough to expand beyond basic PoCs when you’re trying to implement compliance automation.
Guess what? Now is when you get the guidance on how to actually make it work!
Most GRC automation content focuses on selecting tools and technologies. The reality is that successful enterprise implementation depends more on organisational dynamics, stakeholder coordination, and architectural decisions than on specific platforms or programming languages.
Pulling from direct experience and working with GRC leaders across industries, the difference between proof-of-concept success and production sustainability comes down to understanding that automation is fundamentally a systems integration and change management challenge, not just a technical one. This framework distils those lessons into actionable steps that prevent the common traps of over-engineering, stakeholder alienation, and parallel infrastructure creation.
Step 1: Map Your Current State
Document existing control testing processes and stakeholder touchpoints
Identify which security teams already collect the data you need
Catalogue your audit evidence requirements and external validator expectations
Output: Clear inventory of processes, data sources, and stakeholder relationships
Area | Questions to Answer | Output |
|---|---|---|
Processes | How do we currently test controls? What evidence do we collect? How long does each control take? | Process documentation with time estimates |
Data Sources | Which security teams collect similar data? What tools do they use? How often is data refreshed? | Data source inventory with ownership |
Stakeholders | Who are the control owners? What do auditors require? Who maintains the security tools? | Stakeholder contact matrix |
The foundation of successful automation isn't technical architecture - it's understanding what you're actually trying to improve. Most GRC teams rush to solutions without mapping the complex web of existing processes, data flows, and stakeholder relationships that determine whether automation will create value or chaos. This step prevents the common trap of building parallel infrastructure that duplicates work already happening in security teams whilst creating coordination bottlenecks rather than eliminating them.
Step 2: Choose Your Integration Strategy
Select boring, maintainable solutions over complex policy engines
Design for multi-framework support from the start
Output: Technical architecture decision and stakeholder agreement
Factor | Work Through Existing Tools | Build Direct Integration |
|---|---|---|
Data Quality | Production-grade, battle-tested | Unknown until implemented |
Maintenance | Security team handles updates | GRC team owns all maintenance |
Context | Full security context included | Limited to compliance view |
Reliability | Proven uptime and monitoring | Custom monitoring required |
Stakeholder Relations | Collaborative partnership | Potential coordination friction |
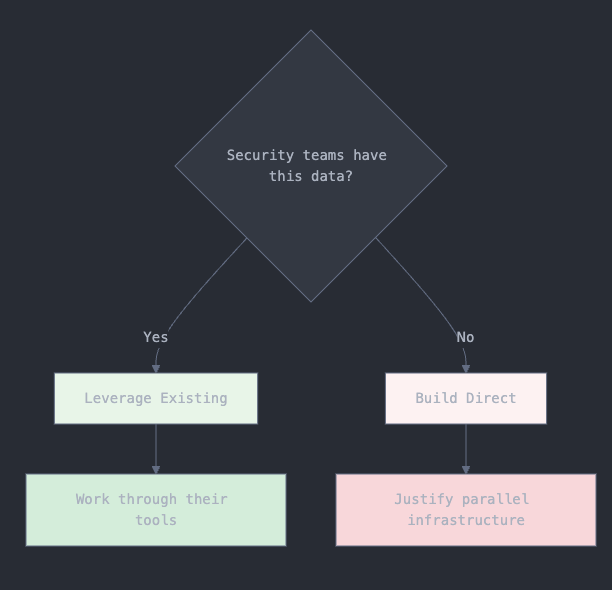
Your integration strategy determines whether you become a force multiplier or a coordination burden. The temptation to build sophisticated policy-as-code implementations often leads to maintenance nightmares that neither GRC nor engineering teams want to own. Instead, focus on leveraging data that security teams already collect through their operational workflows. This approach builds on proven production systems rather than creating new technical debt whilst maintaining the collaborative relationships essential for long-term success.
Step 3: Build MVP with Single System Coverage
Start with one security tool that covers multiple controls simultaneously
Focus on data extraction and storage before building complex analysis
Implement historical tracking to address auditor requirements
Output: Working proof-of-concept with measurable control coverage

System Selection Criteria
Factor | Weight | Questions |
|---|---|---|
Control Coverage | High | How many controls can this system address? |
Existing Usage | High | Does security team already use this? |
API Maturity | Medium | Is the API stable and documented? |
Data Quality | Medium | How reliable is the data? |
Integration Complexity | Medium | What's the technical implementation effort? |
Maintenance Burden | Low | Can we maintain this ourselves? |
The system-based approach proves its value during implementation. Rather than automating controls individually, focus on comprehensive integration with security tools that provide broad coverage. This delivers higher return on engineering investment whilst demonstrating clear business impact to stakeholders.
The key insight: spending significant time on one system that automates multiple controls creates more sustainable value than quick wins on isolated control points.
Step 4: Validate with External Stakeholders
Test audit evidence formats with external validators early
Iterate based on compliance team feedback, not technical preferences
Measure stakeholder disruption and adjust integration approach accordingly
Output: Auditor-accepted evidence collection process

Common Auditor Concerns and Responses
Auditor Concern | Technical Response | Documentation Needed |
|---|---|---|
"How do we know data is current?" | Timestamp every data extraction | API call logs with frequency documentation |
"What if automation fails?" | Automated failure detection and alerting | Exception handling procedures and escalation paths |
"Can data be manipulated?" | Read-only access with audit trails | Authentication logs and access control documentation |
"How do we validate accuracy?" | Sample manual verification process | Regular reconciliation between automated and manual evidence |
External validation requirements constrain technical implementation in ways that purely internal projects don't face. Auditors care about evidence freshness, chain of custody, and documentation standards that may seem bureaucratic but determine whether your automation actually reduces audit preparation effort. Testing these requirements early prevents the common scenario where technically successful automation fails to meet external compliance needs, forcing teams to maintain manual processes alongside automated systems.
Step 5: Scale Based on Proven Value
Expand to additional systems only after demonstrating clear ROI from initial implementation
Prioritise automations that save the most human hours across the most team members
Build integration with existing GRC platforms for centralised reporting
Output: Production-ready automation serving multiple compliance frameworks

Scaling Decision Matrix
System | Controls Covered | Hours Saved/Cycle | Implementation Effort | Priority Score |
|---|---|---|---|---|
CSMP Platform | 12 | 40 | Medium | High |
Identity Provider | 8 | 30 | Low | Medium |
SIEM Platform | 6 | 20 | High | Low |
Application Security Tools | 10 | 25 | Medium | Medium |
Priority Calculation: (Hours Saved × Controls Covered) / Implementation Effort = Priority Score
Scaling requires discipline to avoid the "automation maximalist" trap where teams try to automate everything rather than focusing on highest-impact opportunities. The success criteria should be measurable time savings for the largest number of stakeholders, not technical sophistication or comprehensive coverage. This approach builds sustainable automation programmes that generate continued organisational support whilst avoiding the coordination complexity that kills many well-intentioned GRC engineering initiatives.
When are you starting your journey?

Enterprise GRC automation succeeds when it addresses organisational complexity through systematic process improvement, not when it chases technical sophistication for its own sake. The organisations that need GRC engineering most are precisely those with complex, heterogeneous environments that can't be solved as easily as in smaller cloud-native companies.
The framework presented here prioritises sustainable business value over impressive technical demonstrations. It recognises that successful automation requires stakeholder alignment, process maturity, and systems thinking about coordination costs - not just API integrations and policy-as-code implementations.
The choice isn't whether to automate GRC processes. The choice is to build systems that work with your actual enterprise complexity. Start with Step 1.
Map what you actually have before building what you think you need.
Which evidence collection processes could you systematise through existing security toolchains this quarter instead of building new technical infrastructure?

Did you enjoy this week's entry? |

What I’ve been consuming 🎧
Resources I’ve been consuming which are relevant to GRC Engineering!
Just dropped the surprise GRC Engineer Podcast episode with Varun Gurnaney
This episode was literally over a year in the making - the man is notoriously difficult to get hold of, but absolutely worth the wait. It's actually fairly unscripted and is a candid conversation between two GRC practitioners.
Varun brings a rare perspective to our industry, he's a proper software engineer who chose to tackle GRC problems and co-author of the GRC Engineering Manifesto. His technical depth combined with his philosophical takes on compliance make for some truly thought-provoking discussions.
What he also brings is a truckload of hot takes, a selection here:
🔥 "I don't think you need a compliance team. You should get a great security team and an auditor liaison."
🔥 "I think compliance should be free. I think you and I should not have jobs." (Thanks for that, Varun!)
🔥 "Humans are made for better things than for an ISO checklist."
🔥 "SOC 2 is a sales tool. SOC 2 is not a security tool. It's a sales thing."
🔥 "Will you stop buying IKEA desks if they don't have an ISO? No, I'll still buy an IKEA desk."
🔥 "Screenshots are cool again. We can use OpenAI operator, just like go take screenshots."
🔥 "GRC folks, this is the time you can switch to an engineering role. Coding agents have never made it easier."
Varun's blog posts on Medium are brilliant, and his engineering-first approach to compliance problems offers fresh perspectives our industry desperately needs.
Check out the podcast and connect with Varun!

That’s all for this week’s issue, folks!
If you enjoyed it, you might also enjoy:
My spicier takes on LinkedIn [/in/ayoubfandi]
Listening to the GRC Engineer Podcast
See you next week!

Reply